20+ siem network diagram
6 to 30 characters long. In this mechanism the client and server.

Overview Of A Siem Architecture Showing Some Of The Core Facility Download Scientific Diagram
BigPanda has more than 20 microservices running in production with a large AWS deployment that generates 30 GB of log data every day.

. A dataset is a component of a data model. An intrusion detection system IDS. The sales and customer success teams at.
In control engineering a state-space representation is a mathematical model of a physical system as a set of input output and state variables related by first-order differential equations or difference equationsState variables are variables whose values evolve over time in a way that depends on the values they have at any given time and on the externally imposed values of. The above technologies and solutions will continue to improve auto-remediation self-healing infrastructure event correlation and predictive analytics. Network Resolution DNS The fields and tags in the Network Resolution DNS data model describe DNS traffic both serverserver and clientserver.
Output to a json syslog CEF or LEEF local file your SIEM or other tools would have to actively read from that file Output to syslog CEF or LEEF to a syslog listener most modern SIEMs have a built in syslog listener Here is a flow diagram of how to pick the right configuration file. For example if the local on-premises network has a 1921681024 address space and one of the virtual networks has a 1050016 address space then we would need an access list entry from the local network to the virtual network which we typically would have already setup and another access list entry from the 1050016 virtual network. For technical support and breakfix questions please visit.
Smart Protection Network - Smart Feedback. The CIM is implemented as an add-on that contains a collection of data models documentation and tools that support the consistent normalized treatment of data for maximum efficiency at. The following diagram explains about how different Azure built-in roles work.
Runtime Aware Network Policy. Overview of the Splunk Common Information Model. 514Syslog over UDP SIEM or syslog server port.
Be sure to also check out the Microsoft 365 community. SIEM solutions for AWS Control Tower monitor workloads in real-time identify security issues and expedite root-cause analysis. Tags used with the DNS event dataset.
Learn about Power BI architecture with diagram Essential Components Power BI Desktop PowerBI Gateway Report Server etc. Power BI Desktop is a free desktop application that can be installed on your computer. Its Working Services in detail and more.
Next Generation SIEM with SSC Data Lake. The SIEM connector can. Microsoft continues to work with partners and customers to expand our knowledge of the threat actor behind the nation-state cyberattacks that compromised the supply chain of SolarWinds and impacted multiple other organizations.
What is the three-way handshake. The network diagram can be drawn by LANmanager LANstate Friendly pinger Network view. For details see the table below the diagram.
It comes as part of the Microsoft Office software suite. Define the Visio diagram. Must contain at least 4 different symbols.
Azure Traffic Manager directs the user requests to the nearest data centers and Azure Content Delivery Network CDN allocates the statice filescontent to the users or. A three-way handshake also known as TCP-3way handshake is a mechanism to establish a connection between the client and server over a TCPIP network. Proxies act as an intermediary between two networking devices.
For details see Deploy Secure Tunnel. Visio is a Microsoft Windows diagramming software that enables people to create building plans control charts visualisations flow diagrams organisation charts maps and more. Welcome to the Office 365 discussion space.
You are possibly familiar with Kubernetes NetworkPolicies that define the allowed and denied network communication for Kubernetes workloads. We provide assignment help in over 80 subjects. Oversimplified these policies describe that pod A is allowed to talk to pod B or CIDR 100008 but pod A is not allowed to talk to pod C or CIDR 2011132.
Microsoft previously used Solorigate as the primary designation for the actor but moving forward we want to place. Central Policy Manager CPMCPM changes passwords automatically on remote machines and stores the new passwords in the Privilege Cloud vault with no human. A dataset is a component of a data model.
It cohesively works with the Power BI service by providing advanced data modeling shaping exploration and creating reports with highly interactive visualizations. The Splunk Common Information Model CIM is a shared semantic model focused on extracting value from data. In versions of the Splunk platform prior to version 650 these were referred to as data model objects.
Simplified diagram showing how AMSI detections in a few machines are extended to other customers via the cloud. A proxy can protect the local network. 200 and later agents appliances connect to.
They handle primary SIEM challenges. We will take care of all your assignment needs. The Privilege Cloud Secure Tunnel enables you to securely connect Privilege Cloud with your LDAP and SIEM servers.
The SIEM approach includes a consolidated dashboard that allows you to identify activity trends and patterns. The diagram below illustrates a proposed next generation SIEM supported by a centralized SSC Data Lake. Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system.
SIEM is an approach to enterprise security management that seeks to provide a holistic view of an organizations IT security. ASCII characters only characters found on a standard US keyboard. The main purpose of SIEM is to provide a simultaneous and comprehensive view of your IT security.
In Windows Defender AVs cloud-delivered antivirus protection the Office VBA and AMSI integration enriches the signals sent to the cloud where multiple layers of machine learning models classify and make verdicts on. Which is a network interface that connects you privately and securely to a service powered by Azure Private Link. The following diagram shows the default ports in a Deep Security system.
They keep SOPs and SOC processes up to date and improve them. In versions of the Splunk platform prior to version 650 these were referred to as data model objects. This is the place to discuss best practices news and the latest trends and topics related to Office 365.
We recommend you to use private endpoints for secure backup and restore without the need to add to an allowlist of any IPsFQDNs for Azure Backup or. Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations. We are a leading online assignment help service provider.
Explain about Power BI Desktop. The fields and tags in the Network Traffic data model describe flows of data across network infrastructure components. Draw a network diagram about the organization that helps you to understand logical connection path to the target host in the network.
In OpenSearch Dashboards select log-aws-securityhub- or log-aws-vpcflowlogs- or log-aws-cloudtrail- or any other index patterns and add eventmodule to the display fieldeventmodule is a field that indicates where the log originates fromIf you are collecting other threat information such as Security Hub log-type is Security Hub and eventmodule.

Security Information And Event Management Siem Component Download Scientific Diagram
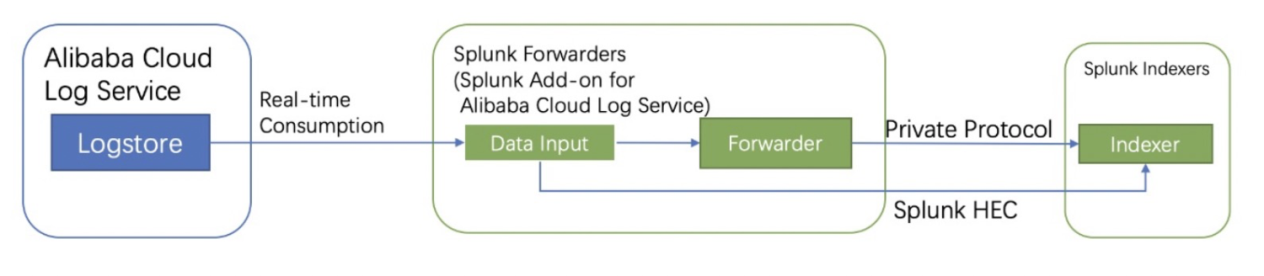
Build A Cloud Siem Scheme Based On The Sls Platform And Log Audit Alibaba Cloud Community
Flowchart Showing Siem Architecture For Cyber Kill Chain Model Download Scientific Diagram
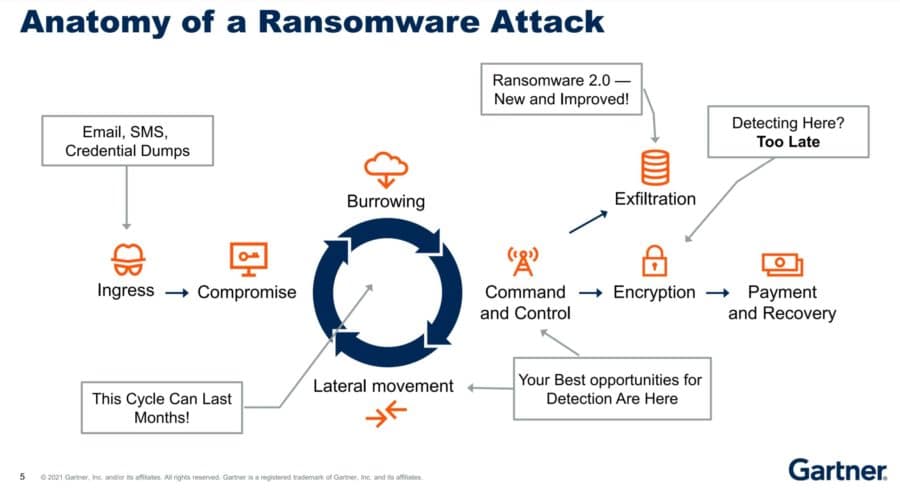
Cybersecurity Mesh And Decentralized Identity Explained

Siem Agents Polling Or Pulling Architecture Download Scientific Diagram

11 Best Siem Tools To Secure Your Organization From Cyberattacks

U S Security Agencies Release Network Security Vulnerability Guidance Esecurityplanet

Comprehensive Explanation What Is A Siem In 2020 And Beyond Detectx Cloud Security Expert

A Classical Architecture Of A Siem System Download Scientific Diagram

How To Effectively Deploy A Siem System Siem As A Service System Deployment Anomaly Detection

A Classical Architecture Of A Siem System Download Scientific Diagram
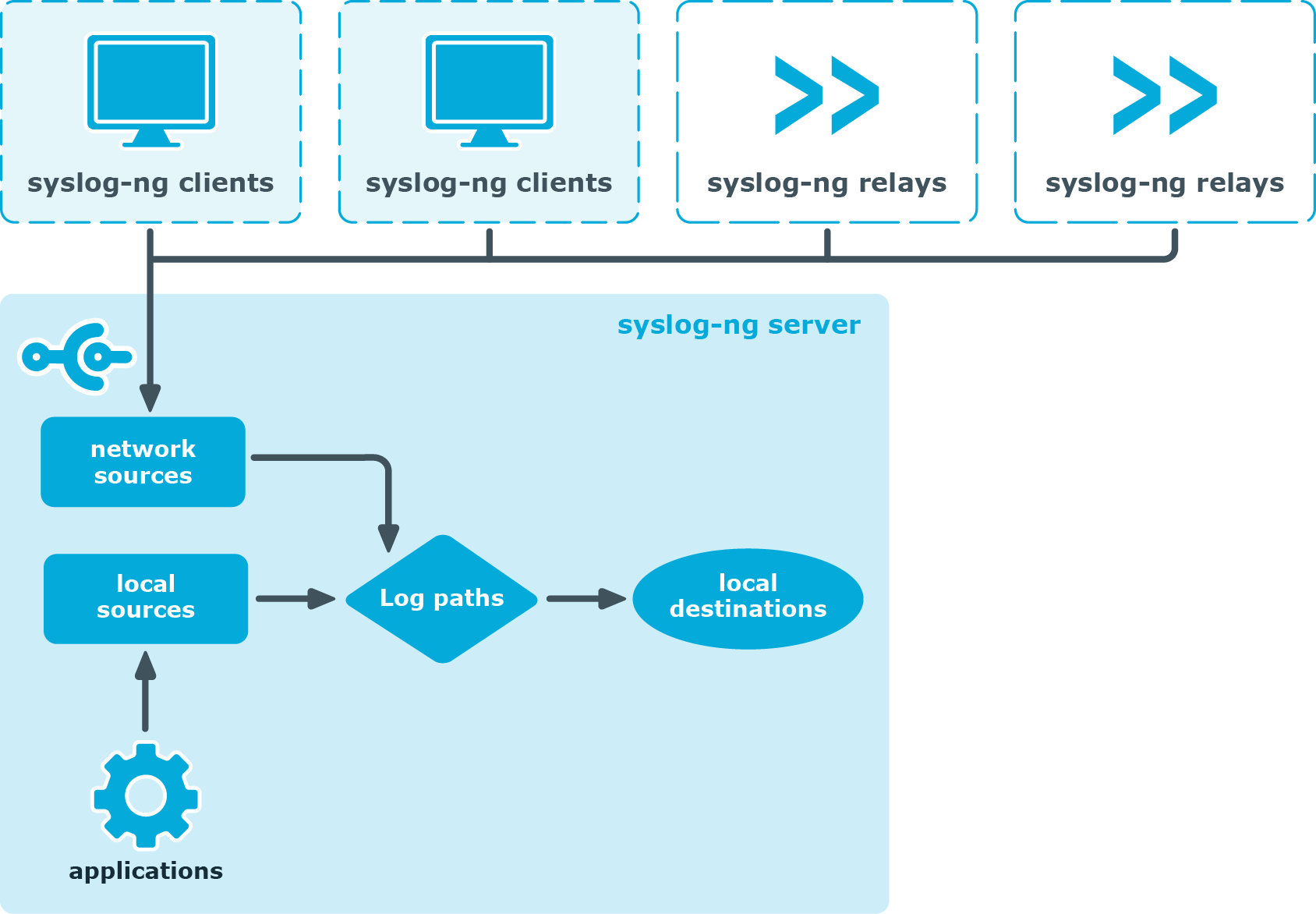
20 Best Log Management Tools Monitoring Software 2022 Sematext
Experimental Setup For Security Onion Secon Deployment For The Siem Download Scientific Diagram

Export Google Cloud Security Data To Your Siem System Google Cloud Platform Community

The Latest Version Of Arcsight Siem

Logging And Monitoring Security Foundations Google Cloud

Security Information And Event Management Siem A Detailed Explanation Event Management Management Software Security